Identity Review | Global Tech Think Tank
Keep up with the digital identity landscape.
Virtual private networks, known colloquially as VPNs, are network connections based on virtual tunnels. Its background begins in 1996, when a Microsoft employee started developing a Peer to Peer Tunneling Protocol (PPTP) as an improvement to the PPP standard, which lacked tunneling. PPTP was formally published in 1999 and has been a trusted source of security since.
VPNs were originally not meant for the average computer user, but instead for large corporations, who needed a secure and private method of communication between different offices not connected to a physical network. Around 2005, VPN providers entered the market in order to provide the technology to regular consumers. VPNs serve as “another perimeter, more closely managed than the network it is situated in.” The activity on the VPN is typically encrypted, but it is difficult to secure VPNs because they give users access to the entire network and they only have a perimeter level of security.
VPNs, likewise, must be configured by hand and are also expensive to manage with licensing agreements. It remains difficult to scale VPNs—as more devices are added to the network, the connection speed slows down for current users. In fact, the most common complaints about VPNs are their lagging connection speeds. Remote workers often noticed the difficulties of using video conferencing platforms such as Zoom or Skype over VPNs during the pandemic, noting the unreliable connections.
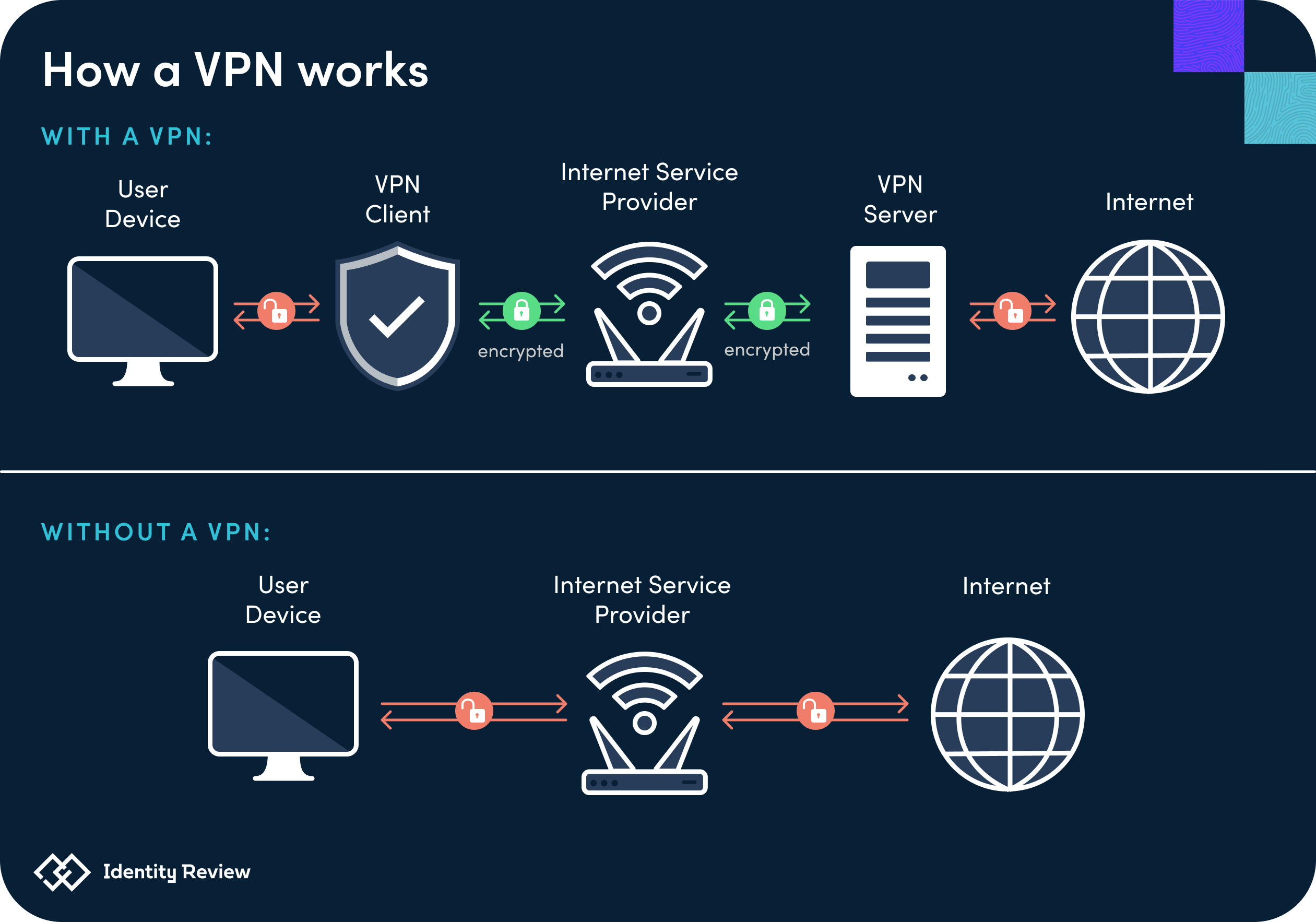
Virtual private networks remain in the market today, but there are still widespread security concerns. Because these virtual connections generally only secure the perimeter of the network, they leave inner digital assets vulnerable once a user gains remote access.
1. ExpressVPN: Recently winning Editor’s Choice Award for best VPN on CNet, Express VPN currently operates in over 90 countries and has a kill-switch feature that prevents network data from leaking outside of the VPN tunnel. The VPN is backed by TrustedServer technology, which ensures that users’ online activities are not logged or tracked. The VPN even allows for Bitcoin as a payment option, adding an extra layer of privacy during checkout.
2. Surfshark: Surfshark is among the more affordable VPN options, priced at $2.49 a month for a two-year plan. Though smaller than some of its network competitors, the VPN is known for its reliable and quick access methods. The company has over 3,200 servers spread across 65 countries, operating on Mac, Windows, iOS, Android and smart TV’s. Among their more unique offerings is its whitelisting capabilities—granting users exclusive access to certain websites, applications, and IP addresses and allowing them to bypass security systems.
3. NordVPN: By providing 6 simultaneous connections through the network, NordVPN outperforms several other companies, who most often only offer 5 connections. Similar to ExpressVPN, the company also offers a kill-switch feature.
4. ProtonVPN: ProtonVPN stands out for its high base speed. The company has 1,259 servers across 55 countries, and their VPNs are completely open source, with several published audits for transparency. Critics, however, point out the platform’s price: $8 per month, which is higher than other companies such as ExpressVPN or Surfshark.
5. IPVanish: For newcomers, IPVanish is among the best options. The interface is easy to configure and requires only $3.75 per month — ideal for those on a budget and with less technical experience. IPVanish boasts its own kill-switch feature, important for user privacy while connecting to the VPN.
Zero Trust Networks are based on the Zero Trust Security Model developed by Forrester analyst John Kindervag in 2010. It has since been adopted by major tech companies such as Microsoft, Cisco and Palo Alto Networks. According to the model, “every user and connection should be verified before accessing IT resources, regardless of where the connection originates.”
The network operates by assuming each device is not authorized for network access and will individually authenticate each network connection request. Unlike VPNs, Zero Trust Networks limit the network “surface area,” providing more scalability. These networks follow the least privileged access model, meaning that users can only access the data that is necessary for what they need to do at work. This differs from VPNs, which rarely restrict content access once a user connects to the network.
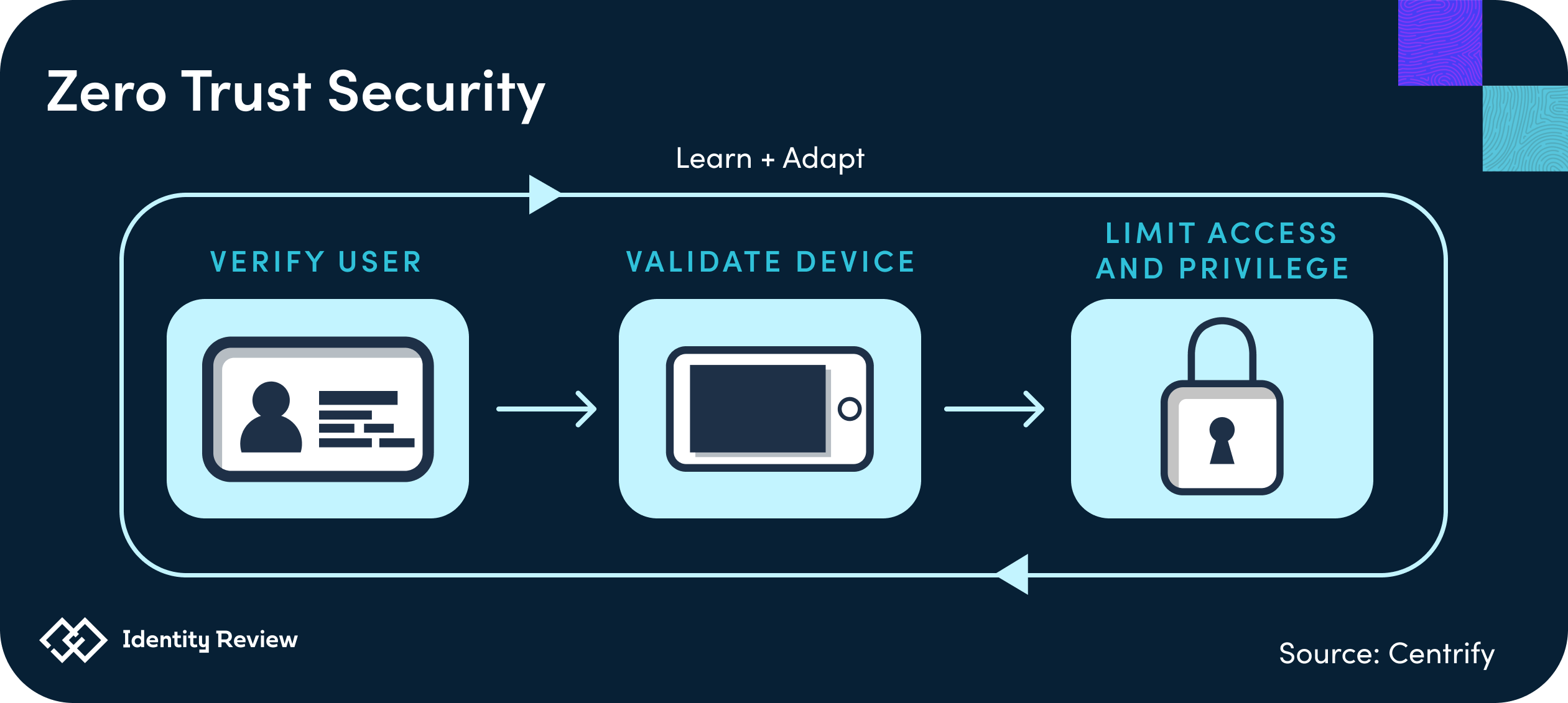
Companies saw a sizable shift to zero trust networks recently—60% of companies believe that the pandemic sped up their adoption of zero trust networks, and over 90% had some level of success implementing them. Unlike VPN’s, trust networks have advanced user authentication processes, often requiring answers to security questions along with the traditional username and password. Because of this, malicious actors impersonating authorized users can often be detected easier. Companies that use trust networks need to inspect and log all network activities using Security Information and Event Management (SIEM) systems such as Splunk or Microsoft Azure Sentinel.
1. IBM: IBM provides flexible zero trust solutions for cloud, user privacy, insider threats and hybrid work. By comparing client’s current security gaps against their zero trust governance model, IBM’s team helps clients implement zero trust compliances into their current security solutions.
2. Ivanti: Ivanti is an industry leader in unified endpoint management, zero trust security and service management solutions. Ivanti Neurons, their foremost solution, is powered by advanced machine learning and deep intelligence methods, and at large their products proactively resolve up to 80% of endpoint issues. By “boosting your bottom line,” Ivanti provides daily security insights that enables users to minimize risks in seconds—they can even reduce unplanned outages by up to 60%.
3. Citrix: With a zero-trust network solution that allows companies to transform their current network configurations on one platform, the Citrix Workspace, recognized by Forrester, has advanced endpoint protection capabilities. The platform’s all-inclusive technology permits businesses to implement the zero trust framework and avoid any security gaps that can come from mixing several different technologies. The platform likewise allows for remote network access without a VPN.
4. Centrify: Centrify’s Zero Trust Privilege offering is a unique solution that secures enterprises from privileged access abuse, a leading cause of data breaches. Privileged access management is the main focus of Centrify—it allows them to deliver “battle-proven and fastest time-to-value solutions,” supporting more than 450 platforms and 2000 companies around the world.
5. Akamai: Used by many business leaders, Akamai supplies zero-trust with advanced identification verification processes. The platform allows for user and device tracking to ensure comprehensive endpoint security, alongside malware protection, centralized IT resources and secure application access.
Do you have information to share with Identity Review? Email us at press@identityreview.com.