Identity Review | Global Tech Think Tank
Keep up with the digital identity landscape.
In the current age of remote work and device-driven lives, cybersecurity has been more pertinent than ever for companies to stay on top of. Managing and orchestrating tens of thousands of devices while also ensuring that all device and server connections are secure has proven to be an extremely difficult and high-stakes task, and so, new and innovative cybersecurity solutions have recently come to light.
Last month, zero-trust networking and software-defined access company Elisity, Inc. announced Elisity Cognitive Trust (ECT). After working in stealth mode for the past 18 months to assemble a team composed of cybersecurity veterans from Cisco, vIPtela, Qualys and more, Elisity hopes to use digital identity as a new defining framework for companies and organizations to transform, modernize, and fortify their enterprise security models through the release of their new identity-based solution.
The COVID-19 pandemic has led to a new era of remote work for employees around the world. For people to be able to continue their work from home, though, they must be able to access the same resources and data that they would typically have access to in their physical workplace, which has presented a number of difficulties for security administrators.
One difficulty of modern-day remote work is that workplace security administrators have tens of thousands of devices to manage, between personal computers, company servers, cloud and multi-cloud servers, smart phones, tablets, and anything else workplace employees may be using to complete their work. As time goes on, more and more devices will add themselves to the pile, and so, companies are realizing that current security solutions are not scalable. There is a new need for automation, consolidation, and improved orchestration and management of these devices within companies.
Another difficulty comes from the increased use of VPNs for remote employees to be able to access important internal resources as they would from being on a company server or network. Ensuring that VPN connections are secured from end-to-end is of paramount importance, as the moment one user’s device is compromised while connected to a company VPN, cyberattackers have access to anywhere they wish to go.
Even after the pandemic comes to an end, the age of remote work will continue on. Therefore, it is essential that companies find new, scalable, and adaptable cybersecurity solutions to ensure the protection of not only internal company data, but also the data of millions of consumers.
“The era of limited point solutions is over—we’re ushering in a new age of comprehensive, Zero Trust, AI-driven security based on identity. I believe, with the convergence of industry trends and the pandemic on our hands, it is the right time to reimagine the enterprise security landscape,” said Elisity co-founder and CEO Burjiz Pithawala. “Today, the majority of enterprise workers are remote, and are likely to be for some time. Moreover, most organizations will soon have more data and devices outside their networks than inside it. Elisity is here to be a beacon—ushering in an era of smarter, more powerful, and more secure access solutions for the enterprise.”
Elisity Cognitive Trust is a cybersecurity solution that combines the two major security approaches of Zero Trust Network Access and software-defined perimeter technology and powers it through artificial intelligence. According to Pithawala, ECT “enables enterprises to embrace digital transformation and workforce mobility, while securing access with identity-based policy for all users, devices, applications, and data, from one centralized platform.” Essentially, users, devices, and applications are authorized through access policy recommendations that are shaped by user behavior and risk. Therefore, not only does ECT provide an innovative and comprehensive security infrastructure for its users, but it also adapts continuously to company changes through AI.
Through this solution, Elisity hopes to address the problems of authentication and authorization. In terms of authentication, the company is continuously working in the space with authentication companies such as Okta, Ping Identity, Duo, and more to determine the best way to verify a user’s identity when trying to access certain data, resources, or services. However, with fast-paced innovation in the mobile technology and cloud-based technology industries as well as the development of IoT devices, the challenge lies in determining the best way to manage and parse the identity.
This is where the authorization problem comes into play. On top of proving that a user is who they say they are in order to access a certain resource, what is the best way for a user to prove that they are entitled to have said access?
“Twenty years ago, cybersecurity was a $1 billion market. Today, it’s a $135 billion market,” said Shiva Mandalam, Vice President of Product Management at Elisity. “It seems like it’s ever-growing, but the number of cybersecurity attacks has been really consistent. There’s not a day that goes by where you don’t hear things about security in the news.”
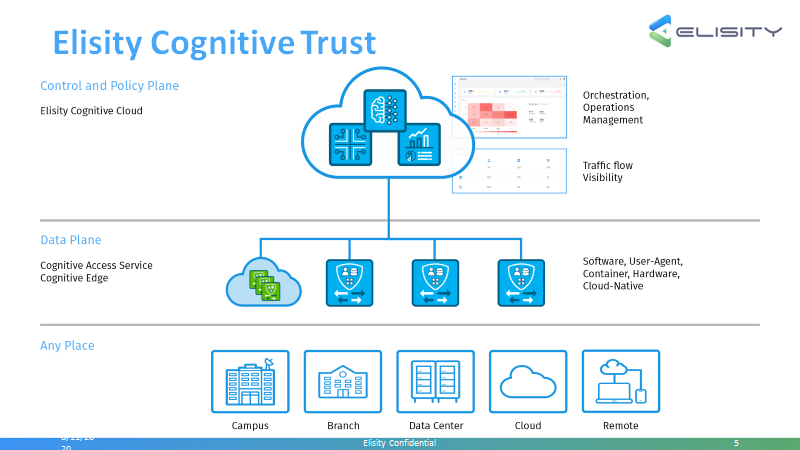
Addressing cybersecurity attacks becomes even more complicated when thinking about the fragmentation of the authorization problem. Users cross domains constantly—when switching between working in wireless networks and wired networks, from cloud computing to remote coming, and more—which means that they have multiple digital identities across different domains. Furthermore, on the policy end, determining the best way to manage multiple identities, users, networks, and domains leads to a high cost of ownership. With Elisity’s new solution, enterprises using the service can realize cost savings, time savings, risk mitigation and more, due to its centralized policy-first and zero-trust approach.
“The real problem we’re trying to hit is one of reducing total costs of deployment and ownership, and just not having silos and siloed approaches which create islands of identity and then forward with that island of security. We’re trying to pave the way of creating an island of security, which includes access and authorization,” said Patel. “We integrate with the ecosystem—with the authentication framework you might already have, and our solution manages the entire identity for the enterprise.”