Identity Review | Global Tech Think Tank
Keep up with the digital identity landscape.
Multi-Factor Authentication (MFA) is an authentication technique that requires users to have 2+ verification tools to gain access to an account, application or VPN (virtual private network). This is a common component of identity access management policies. Access management systems allow companies to manage several types of identities such as humans, hardware, software and even IoT devices.
Traditionally, systems simply ask for a username and password. But usernames and passwords are often subject to brute force attacks—when hackers use an excessive trial and error process to guess possible username and password combinations of a login. MFA asks for other credentials, decreasing the chance of a security breach. For instance, a user name, password, a pin from a security application on a cellphone and a fingerprint scan could be combined to form an MFA chain.
MFA is driven by several types of verification information, otherwise known as factors. One time passwords are common within the MFA process. These passwords are typically 4-8 digit codes that users will receive through email, SMS or a mobile authentication app. The codes are valid for a specific time frame and will reset after every authentication request. Moreover, the codes are created from an assigned value associated with each user when they register, alongside a certain time value that will vary based on the system.
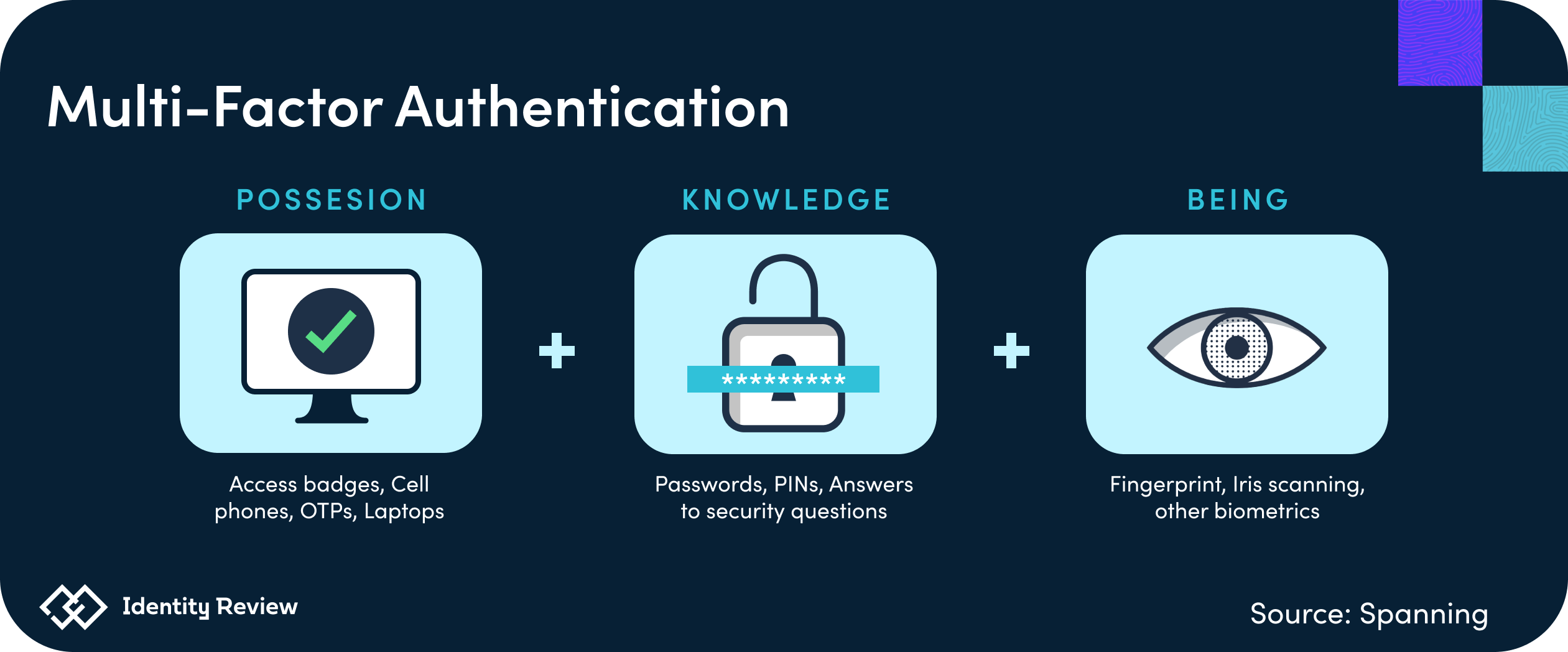
Many MFA methods are based on three specific types of information.
Location-based MFA and adaptive authentication are also valid forms of verification.
Location-based MFA will utilize the user’s IP address and potentially their physical location. Often, this information is used to see if a user’s location is on a company’s whitelist, but could also be used along with one time passwords (OTPs) and/or other factors. Adaptive authentication, or risk-based authentication, will consider user behavior during the security checking process and determine a risk level associated with that user. Some questions used under the adaptive MFA framework include:
Two-Factor Authentication is a subcategory of MFA. It is widely used for digital banking, social media and e-commerce. Consumers commonly encounter 2FA when withdrawing money from an ATM—here, a user inputs a debit card (a factor the user possesses), along with a PIN (a factor the user knows) to successfully gain access. 2FA follows the same factors as MFA (knowledge, possession, inherence), but chooses two instead of multiple.
Single Sign On (SSO) is another common authentication technique that allows users to gain access across multiple applications or websites with a single set of credentials. The SSO framework is based on a trust certificate between the service provider and identity provider. This certificate is typically composed of identifying pieces of information about a user, such as a username or email, ensuring the information being sent to the service provider is from a secure source. The steps of SSO are typically as follows:
Likewise, Challenge Handshake Authentication Protocol (CHAP) is a method that verifies a user to a network with 3-way encryption. First, the network router sends a “challenge” to the remote host, which will send back a response with MD5 encryption. The network router examines the response and if it matches the hash value, it will authenticate the connection. This is more secure than the traditional username and password as the network can send a “challenge” at any point, while usernames/passwords are only used during initial authentication.
Do you have information to share with Identity Review? Email us at press@identityreview.com.